1. DevC++ Download
2.Rcd Logger DOWNLOAD UDAH DI PERBAIKI
3.kopi satu gelas....
4.otak yg encer..
Product Name : RCD Logger 3.0
Used Module : BASSMOD, BRD - Teleport Prokg.xm, FindPattern, WriteLog, CreateFileFromResource, ExitProcess, etc...
Released : 11-12-2010
Creator : RCD
Greetz to :
[*] _hrd_
[*] ukira
[*] NoName
[*] DewaPB a.k.a Irvan R.F.O
[*] and many more...
Archive Type : ZIP
Included files : ~>RCDLogger3.0.exe
Game Target : PointBlank
Anti-Cheat : AhnLab HackShield Pro
Type : Addys Logger
Supported Logged :
[*] Minimize1
[*] Minimize2
[*] Wallshot
[*] WallshotNoBT
[*] Ammo
[*] Bomberman
Note Tambahan : Boleh C&P tapi jangan lupa nama pembuatnya !
Cara pemakaian : Simply run RCDLogger3.0.exe and FireUp PBLauncher, logging result will show up after complete logging
MD5 Sum : -
3. RCD base
buat new project install lakukan sperti step di gamba:
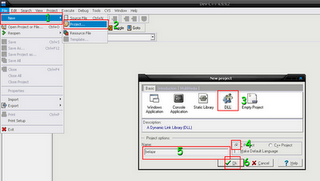
delet semua command di dll.h sama dllmain.c ganti dengan ini
untuk main Dll
/*
Name: RCD Base
Copyright: RCD
Author: RCD
Date: 22/11/10 15:37
Description: SC Dasar untuk lebih mudah menggunakan RCD Logger
===============================================================
Edited by Hero™ 2010/12/14
*/
#define WIN32_LEAN_AND_MEAN //buang yg tidak berguna
#include "dll.h" // sumber offset dan deklarasi dll
#include // include untuk createthread
#include
#include
LPTSTR ModulGame = "PointBlank.i3Exec";
//////////////assembly /////////////////////
void Patch(void *adr, void *ptr, int size)
{
DWORD OldProtection;
VirtualProtect(adr,size,PAGE_EXECUTE_READWRITE, &OldProtection);
memcpy(adr,ptr,size);
VirtualProtect(adr,size,OldProtection, &OldProtection);
}
DWORD WINAPI MemPacth(LPVOID param) // Perulangan
{
while (1) { // Jika nilai 1 atau True jalankan fungsi dibawah ini !
// AltTab On
if (GetAsyncKeyState(VK_INSERT)&1) {
MessageBeep(0);
DWORD adrMin1, adrMin2 = 0;
DWORD dwPB = (DWORD)GetModuleHandleA(ModulGame);
if (dwPB > 0) {
adrMin1 = dwPB + (DWORD)OFS_MIN1;
Patch((void *)(adrMin1),(void*)(PBYTE)"\x00", 1);
adrMin2 = dwPB + (DWORD)OFS_MIN2;
Patch((void *)(adrMin2),(void*)(PBYTE)"\x00", 1);
MessageBox (0,"MINIMIZE ON....jgn sering2 ajah","AWASS!!!!", MB_TOPMOST);
beep (1000,500);
}
}
// Altab Off
if (GetAsyncKeyState(VK_DELETE)&1) {
MessageBeep(0);
DWORD adrMin1, adrMin2 = 0;
DWORD dwPB = (DWORD)GetModuleHandleA(ModulGame);
if (dwPB > 0) {
adrMin1 = dwPB + (DWORD)OFS_MIN1;
Patch((void *)(adrMin1),(void*)(PBYTE)"\x01", 1);
adrMin2 = dwPB + (DWORD)OFS_MIN2;
Patch((void *)(adrMin2),(void*)(PBYTE)"\x01", 1);
beep (1000,500);
}
}
// WallShoot ON
if (GetAsyncKeyState(VK_HOME)&1) {
MessageBeep(0);
DWORD adrWall = 0;
DWORD dwPB = (DWORD)GetModuleHandleA(ModulGame);
if (dwPB > 0) {
adrWall = dwPB + (DWORD)OFS_WALL;
Patch((void *)(adrWall),(void*)(PBYTE)"\xC3", 1);
beep (1000,500);
}
}
// WallShoot OFF
if (GetAsyncKeyState(VK_END)&1) {
MessageBeep(0);
DWORD adrWall = 0;
DWORD dwPB = (DWORD)GetModuleHandleA(ModulGame);
if (dwPB > 0) {
adrWall = dwPB + (DWORD)OFS_WALL;
Patch((void *)(adrWall),(void*)(PBYTE)"\x55", 1);
beep (1500,500);
}
}
// BOM ON
if (GetAsyncKeyState(VK_PRIOR)&1) { // tombol page up
MessageBeep(0);
DWORD adrBom = 0;
DWORD dwPB = (DWORD)GetModuleHandleA(ModulGame);
if (dwPB> 0) {
adrBom = dwPB + (DWORD)OFS_BOM;
Patch((void *)(adrBom),(void*)(PBYTE)"\x00", 1);
beep (1000,200);
}
}
// BOM OFF
if (GetAsyncKeyState(VK_NEXT)&1) {//tombol page down
MessageBeep(0);
DWORD adrBom = 0;
DWORD dwPB = (DWORD)GetModuleHandleA(ModulGame);
if (dwPB > 0) {
adrBom = dwPB + (DWORD)OFS_BOM;
Patch((void *)(adrBom),(void*)(PBYTE)"\x01", 1);
beep (1500,200);
}
}
Sleep(5); // Berikan jeda
}
return (0); // unhook
}
BOOL WINAPI DllMain(HMODULE hDll, DWORD dwReason, LPVOID lpReserved)
{
DisableThreadLibraryCalls(hDll);
if(dwReason == DLL_PROCESS_ATTACH){
MessageBox(0,"Your Text Here..............","Head message|Hero", MB_TOPMOST);//notice selalu di atas
CreateThread(0, 0, (LPTHREAD_START_ROUTINE)MemPacth, 0, 0, 0);
system("start http://www.x-lonz.indonesianforum.net);//open url
//kuncinama
char strDLLName [_MAX_PATH];
GetModuleFileName(hDll, strDLLName , _MAX_PATH);
if (strstr(strDLLName, "belajar.dll") <= 0) {//nama dll asli // tampilkan pesan, kalo dll nya sdh bukan asli / sudah di rename MessageBox(0, "Sorry....Dll Hack Not WORKING!!!\nPlease Contact us @forum.us-net.org", "US-Net|Hero™", 0); ExitProcess(0);//PB g jalan } } else if(dwReason == DLL_PROCESS_DETACH) { } return TRUE; }
untuk DLl.h
| #ifndef __RCD_BASE_H #define __RCD_BASE_H #define WIN32_LEAN_AND_MEAN #include void Patch(void *adr, void *ptr, int size); DWORD WINAPI MemPacth(LPVOID param); //DWORD WINAPI LoopHacks(LPVOID param); #endif // ADDYS TEMPELKAN DISINI !!!USAHA dikit aja..... #define OFS_MIN1 0xXXXXXX #define OFS_MIN2 0xXXXXXX #define OFS_BOM 0xXXXXXX #define OFS_WALL 0xXXXXXX |
setelah selesai langusng lakukan seperti gambar di bawah ....

kalo g ada eror jadi tuh dllnya.......
liat di folder project yg tadi disimpan....
credit tutor: US-N:.Hero™
tnx to om rcd dan benZkiller
saya biasa buat DLL menggunakan SC ini tapi kalo g Work silakan gunakan Rcd logger !!!














KK, kog ad errornya y??
BalasHapuspas udah di rebuild all, kesalahan trtunjuk pda Main dll '#include "dll.h" // sumber offset dan deklarasi dll'
setelah dihapus, eh malah LPTSTR ModulGame nya yg salah.. gmn donk?? need ptunjuk..
thxx
ada yang baru gan! silahkan liat"!
BalasHapus